Google had been working on a project called “Passkeys” to replace traditional passwords with a more secure and user-friendly authentication method. However, the details and implementation of Passkeys may have evolved since then. To set up Passkey here’s a general idea of how it might work based on my last update:
Setting Up Google Passkeys
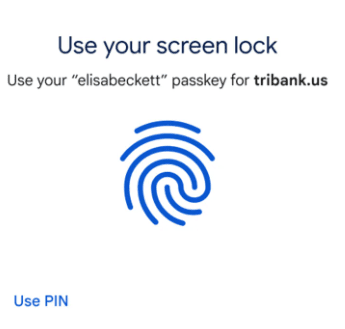
- Ensure Your Device is Compatible: Passkeys may require certain hardware and software features on your device, such as a fingerprint sensor, facial recognition, or biometric authentication.
- Update Your Device: Make sure your device’s operating system and Google apps are up-to-date. Go to the Google Play Store and update the Google app if needed.
- Open Google Settings: On your Android device, open the Google app or go to your device’s Settings and look for the “Google” or “Google Account” section.
- Sign in to Your Google Account: First sign in.
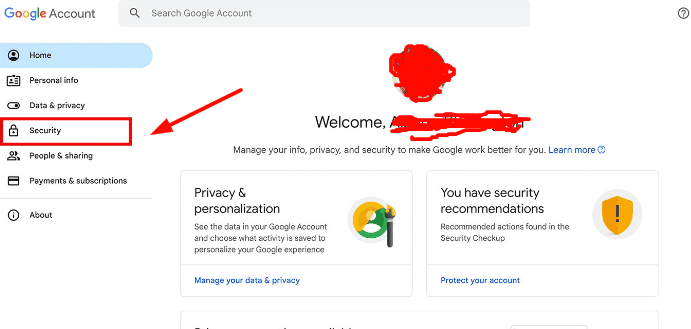
- Security Settings: Navigate to the “Security” or “Security & Privacy” section within your Google Account settings.
- Set Up Passkeys: Look for an option related to Passkeys, password alternatives, or advanced authentication methods.


- Follow On-Screen Instructions: Google will guide you through the process of setting up Passkeys. This may involve configuring biometric authentication (fingerprint, face recognition), creating a PIN, or other methods.
- Verify Identity: You may need to verify your identity during the setup process to ensure the security of your Passkeys.

- Complete Setup: Once you’ve successfully set up Passkeys, they should be ready to use for authentication purposes.
Please note that Passkeys are designed to enhance security and convenience by providing an alternative to traditional passwords. They may not be available on all devices or for all Google Accounts. The specific steps and availability may vary depending on your device, operating system version, and region.
How are passkeys differents from passwords
Passkeys and passwords are both used for authentication purposes, but they differ in their structure, usage, and security features. Here’s how they are different:
1. Structure:
- Passwords: Passwords are typically a combination of letters, numbers, and special characters. They are chosen by users and can vary widely in complexity and length. Passwords can be hard to remember, leading to security issues such as weak or easily guessable passwords.
- Passkeys: Passkeys are generated by the system and are typically longer than traditional passwords. They are often composed of random characters or may be based on cryptographic algorithms. Users don’t choose passkeys; they are provided by the authentication system.
2. User Involvement:
- Passwords: Users create and manage their passwords. This puts the onus on users to choose strong, unique passwords and to remember them. Passwords can be vulnerable to human error, such as choosing weak passwords or reusing them across multiple accounts.
- Passkeys: Users are not directly involved in generating or managing passkeys. Passkeys are often tied to biometric data (e.g., fingerprint or facial recognition) or stored securely on the device. Users are responsible for securing the device itself rather than remembering complex passkeys.
3. Security:
- Passwords: Passwords can be susceptible to various security risks, such as brute-force attacks, dictionary attacks, and phishing attempts. Weak or compromised passwords are a common vector for account breaches.
- Passkeys: Passkeys are generally considered more secure because of their length and randomness. They are less vulnerable to traditional password attacks. Biometric-based passkeys (e.g., fingerprints or facial recognition) can provide an added layer of security.
4. Convenience:
- Passwords: Passwords can be inconvenient for users, as they need to remember multiple passwords for various accounts. Users often forget passwords, which can lead to account lockouts and account recovery processes.
- Passkeys: Passkeys, especially those based on biometrics, offer convenience as users don’t need to remember complex strings of characters. They can simply use their biometric data or a short PIN to unlock their devices or authenticate.
5. Resistance to Phishing:
- Passwords: Traditional passwords are susceptible to phishing attacks, where users are tricked into entering their credentials on malicious websites.
- Passkeys: Passkeys are less vulnerable to phishing because they are typically tied to the device’s hardware and cannot be easily entered on phishing websites.
It’s worth noting that passkeys are part of a broader effort to enhance online security and move away from traditional passwords. They are often used in conjunction with other security measures, such as multi-factor authentication (MFA), to provide robust protection for online accounts.
How passkeys work with operating systems
Passkeys, also known as cryptographic keys or digital keys, serve as a secure means of authentication and encryption across various operating systems and platforms. These keys are generated using cryptographic algorithms and can be used for a range of purposes, such as securing data, authenticating users, and encrypting communications. Here’s how passkeys work across operating systems:
1. Generating Passkeys:
- Passkeys are generated using cryptographic algorithms. These algorithms use random data to create unique, secure keys.
- The length and complexity of passkeys can vary depending on the specific use case and security requirements.
2. Securing Data:
- Passkeys are used to encrypt data, ensuring that it remains confidential and cannot be easily accessed by unauthorized parties.
- When data is encrypted with a passkey, it can only be decrypted using the corresponding key.
3. Authentication:
- Passkeys can be used for user authentication, allowing individuals to prove their identity securely.
- Passkey-based authentication methods may include public key infrastructure (PKI) for secure logins, digital signatures, and secure access to online services.
4. Encryption and Decryption:
- Passkeys are essential for encrypting and decrypting data. To encrypt data, the sender uses the recipient’s public key, while the recipient uses their private key to decrypt it.
- This asymmetric encryption process ensures that data can be securely transmitted and received.
5. Cross-Platform Compatibility:
- Passkeys generated using widely-accepted cryptographic standards are typically compatible across various operating systems and platforms.
- Common cryptographic algorithms and key formats, such as RSA, ECDSA, or AES, are used to ensure compatibility.
6. Secure Communication:
- Passkeys play a vital role in securing communications over the internet. For example, during secure HTTPS connections, web servers use SSL/TLS certificates, which include public keys that are used for encrypting data transmitted to the client.
- The client’s device has the corresponding private key, allowing it to decrypt the data securely.
7. Digital Signatures:
- Passkeys are used to create digital signatures, which verify the authenticity of digital documents, emails, and transactions.
- A private key is used to generate the digital signature, while the recipient can verify it using the corresponding public key.
8. Two-Factor Authentication (2FA):
- Passkeys can be used in 2FA systems, where one factor may be a password or PIN, and the second factor is a cryptographic key or token.
- 2FA enhances security by requiring two different types of authentication.
9. Device Authentication:
- Passkeys are often used in device-to-device authentication, ensuring that devices can securely communicate and exchange data.
It’s important to note that the specific implementation of passkeys and the choice of cryptographic algorithms may vary between different operating systems and platforms. Security standards and protocols are continuously evolving to address emerging threats, so it’s crucial to stay informed about best practices for passkey management and security within the context of your specific operating system or application.
